FREE GUIDE
Get Your Complimentary eBook
When it comes to Vulnerability Management if you want automation, and to standardise things, then you need to have clearly defined rules on how things happen.
What you’ll learn:
This eBook will help you develop your own automation processes and provide suggestions on what to do at each step.
Focus on the elements of automation with suggestions on what to do at each step to be able to develop your own automation process
Understand the link between the four pillars of the S4 Applications vulnerability management programme
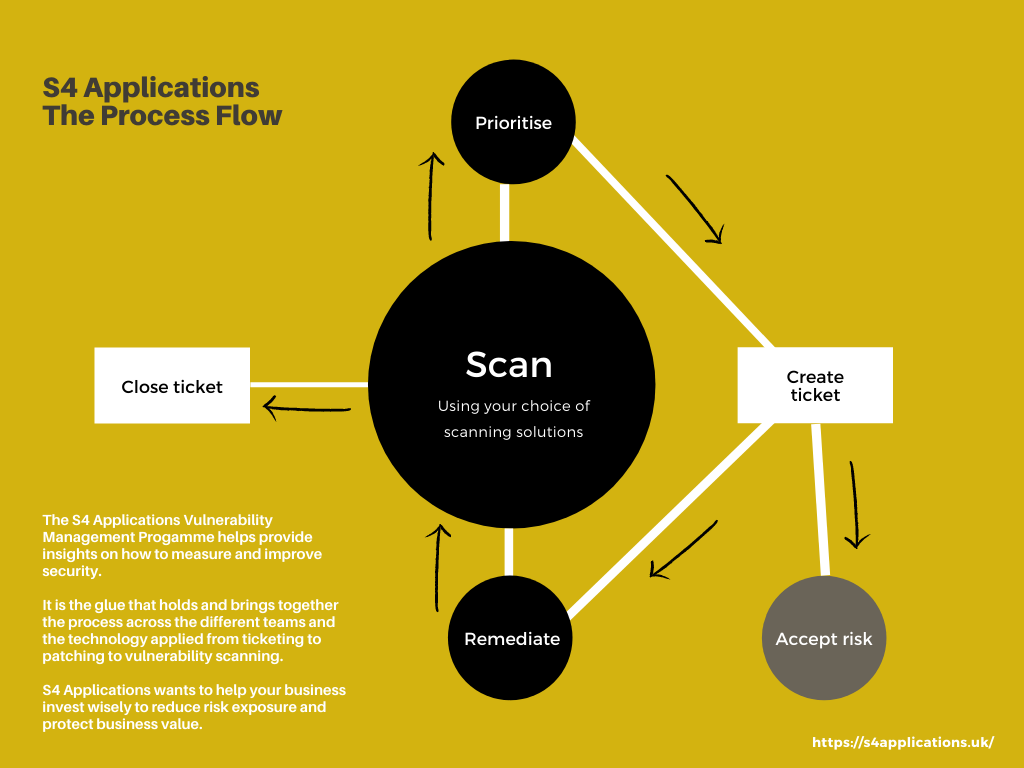
Breakdown of the S4 Applications Process Flow diagram from scan, prioritise, tickets, remediation to risk
The objective of our Vulnerability Management Programme is to provide insights on how to measure and improve security. Download the eBook to learn more about how to set a clear and simple process flow.

Download your free eBook now!

Recommended reading from S4 Applications

No organisation, not even the best, ever gets rid of all their security issues, but they do make an effort to create a complete list of them, and then fix the worst ones. And there is the challenge, what are the “worst ones”? This sounds simple, but is deceptively hard.
Read more ...

Saying “connect to my DAST tool and extract the data” is much easier to write than to implement, as is aligning data from DAST, SAST and network scans into a single, browsable data set that allows you to navigate from application, to server to vulnerability and so on.
Read more ...

As much as things are automated, people don’t always do what you expect in the way you expect; for this reason, you need reports, dashboards and other ways of understanding what has happened to get you where you are now, what is happening at that point in time.
Read more ...